How AI Automation Saved 13 Days per UK Civil Servant in 2024
A recent UK Government AI experiment revealed that certain tasks can be fully automated, saving up to 13 working days per person annually.
The results are documented in two reports: Mapping the Potential by the Alan Turing Institute, and The Government Digital Service’s cross-government experiment of Microsoft 365 Copilot
Between September and December 2024, 20,000 UK civil servants participated in the trial. The findings identified four fully automatable activities:
Revisiting the Letter of Marque
Revisiting the Letter of Marque: Leveraging the Private Sector in Offensive Cyberspace Operations - An Analytical Reflection on Historical Analogies and Contemporary Policy Debates
1. Executive Summary
This policy brief explores a structured model for state-authorized private sector engagement in offensive cyberspace operations. The idea draws inspiration from the historical concept of the letter of marque, which allowed states to authorize private actors to disrupt enemy assets under legal protection. While the 18th-century practice is not directly applicable today, it offers a useful model for assigning limited, accountable roles to private cybersecurity firms in support of national objectives. The brief uses Operation Glowing Symphony—a coordinated U.S. Cyber Command operation targeting ISIS media infrastructure—as a case study. It demonstrates how state-led offensive operations can be developed, rehearsed, and executed in a way that maintains legal oversight and operational discipline. Rather than opening the domain to unregulated hacking, the exploration focuses on enabling authorized and bounded actions against specific non-state threat actors operating below the threshold of armed conflict.
Safeguarding Innovation

On 13 May 2025, I had the privilege of joining the event Safeguarding Innovation in Uncertain Times hosted by Kista Science City, where I contributed a keynote address on the theme of organizational resilience in today’s fragmented and hybrid threat landscape.
I argue that the core challenge companies face is structural, cognitive, and naturally, technological. We operate in a world where power is increasingly diffuse, information is often designed to disorient, and decision-making is hindered by the absence of shared structure.
Rapid, Affordable AI: Transforming Cost, Speed, and Strategic Capability

Artificial intelligence is advancing at an unprecedented pace. A 2019 report by Stanford, McKinsey & Company, Google, PwC, OpenAI, and others revealed that while AI performance once doubled roughly every two years—consistent with Moore’s Law—since 2012, compute has been doubling every 3.4 months. This dramatic acceleration is evident not only in the frequent rollout of new models by tech giants but also in the emergence of innovative competitors.
Policy Implications of State-backed APTs’ Use of AI in Cyberspace

Recent confirmations by Google and OpenAI reveal that state-backed APT groups are increasingly employing AI tools—such as Gemini and ChatGPT—to expedite reconnaissance, malware development, and influence operations. AI-tools have the capabilities to discover zero-days.
Current evidence indicates that several state-sponsored APT groups utilize AI-tools to enhance cyber espionage, phishing, and influence campaigns. Certain threat actors are reportedly employing generative AI for targeted reconnaissance on critical installations, scripting automated attacks, and establishing persistent post-compromise footholds. Similarly, some groups have been observed fabricating job applications to infiltrate organizations under false identities. In contrast, other adversaries, while exploring AI-enhanced malware modification and encryption techniques, appear to engage less with externally developed AI tools—likely due to heightened operational security considerations.
A Sputnik Moment in AI?
Recent debates have focused on whether DeepSeek’s achievement in generating a new model with comparatively limited resources qualifies as a “Sputnik moment” for Western AI companies. This discussion requires distinguishing between developing an entirely new model and adapting pre-existing models. DeepSeek’s approach exemplifies the latter; their methodology involves refining established large language models rather than constructing a new system from scratch.
How do cyber threats impact Canada’s national security, economy, and society?
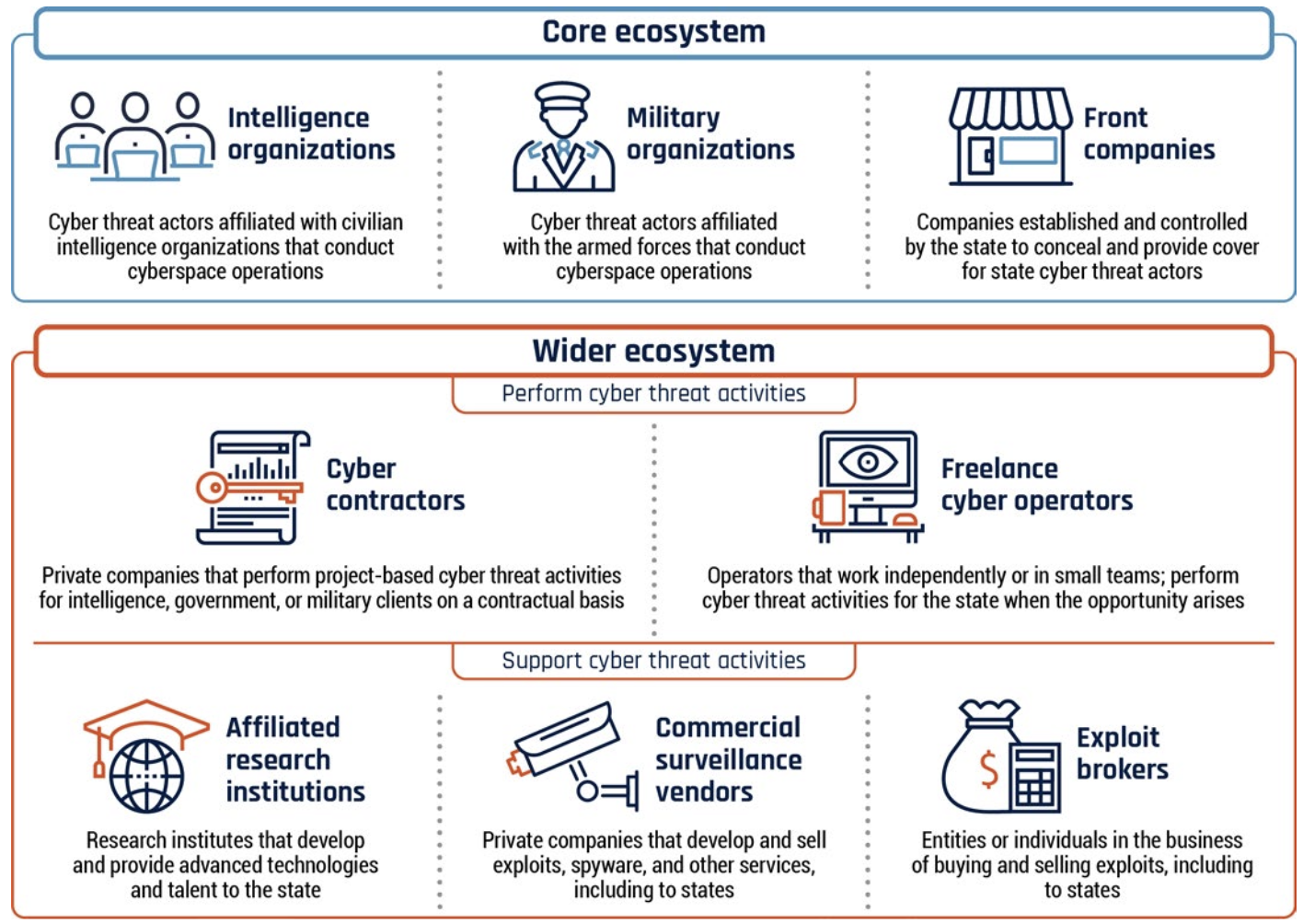
The figure shows the state cyber program ecosystem to “support or perform cyber threat activities.” (Source: CCCS, 2024 p. 10)
The full report is available at the Canadian Centre for Cyber Security.
Canada’s National Cyber Threat Assessment 2025–2026 by the Canadian Centre for Cyber Security (CCCS), part of the Communications Security Establishment (CSE), brings forward an urgent question: How do cyber threats impact Canada’s national security, economy, and society? By examining the range of state and non-state cyber actors, emerging trends, and strategic vulnerabilities, the report provides insights for understanding Canada’s cyber challenges.
Nytt NCSC

Utredningen återfinns på Regeringskansliets hemsida.
Uppdraget är slutfört. Utredaren har överlämnat delbetänkandet “Ett nytt Nationellt cybersäkerhetscenter – Ändamålsenliga och effektiva former för ledning, organisering och styrning”.
Vad betyder detta för NCSC, näringslivet, samhället i stort och Sverige?
Nedan ger jag mina tankar som baseras på utredningens innehåll. Först beskriver jag de utmaningar som NCSC stod inför. I nästa steg presenterar jag de lösningar som rapporten rekommenderar. Därefter utforskar jag vad dessa förändringar kan innebära för näringslivet, samhället i stort, och Sverige. Slutligen reflekterar jag över den bredare betydelsen för det svenska samhället och Sverige i stort.
There is no clear cybersecurity policy

This is a translated English version of the original, which is in Swedish at DI Debatt.
Sweden needs a cyber deterrence strategy and, together with national and international partners, conduct offensive cyber operations against threat actors
A clear Swedish cybersecurity policy is important for deterring cyber threats and showing that attacks have consequences. Examples of a well-designed deterrence strategy can be found in the US, the EU and Australia. In light of the recent ransomware attack that affected more than 120 authorities and businesses, this should also be considered for Sweden.